In the digital realm, your passwords are your fortress against cyber threats. Become a password security ninja and shield your online kingdom from harm.
Ready to fortify your defenses? Let’s secure your realm!
Stay safe online! In this tutorial, we’ll equip you with the knowledge and tips to protect your digital identity. Let’s explore cybersecurity and ensure your online safety!
In the digital realm, your passwords are your fortress against cyber threats. Become a password security ninja and shield your online kingdom from harm.
Ready to fortify your defenses? Let’s secure your realm!

If yes, you should quickly change it. Stay away from using words like “password,” number sequences like “123456,” or simple patterns like “qwerty.” These are the first passwords hackers will try.
The results on the left are real passwords from a study conducted by Nordpass in 2022 from 32 different countries.
Remember, longer is better, so aim for at least 12 characters or more.
Combine uppercase and lowercase letters, numbers, and special characters (e.g., !@#$%^&*) in your password to increase its complexity and resistance against brute-force attacks.
Create strong passwords by using the first letter of each word in a memorable sentence or phrase.
Or by combining random words or phrases that are unrelated and difficult to guess.
You can also substitute letters with numbers or special characters to increase complexity, such as “pUrp13G!tarS0cks” or “B@n@n@JumpCh33s3”.

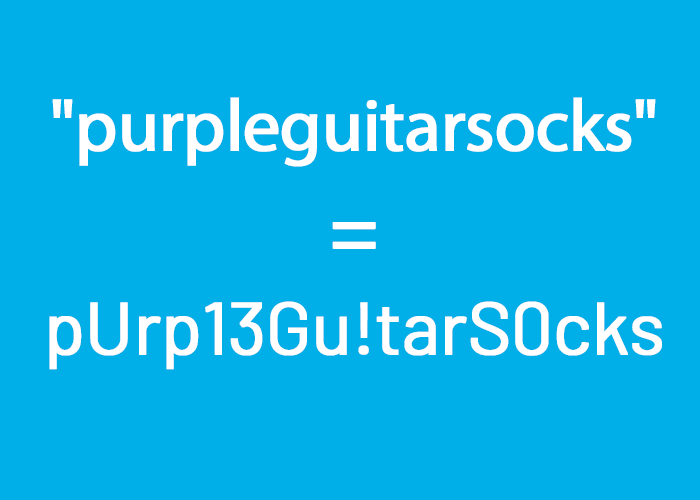
Keep personal details out of your passwords. Don´t put your name or your pet´s name, date of birth, zip code, city, country…
Use a different password for each of your online accounts. You can also use a password manager for added convenience and security. A password manager is a technology tool that helps internet users create, save, manage and use passwords across different online services.
Many browsers offer the possibility to manage passwords, as well as your mobile phone system or a Google account. These managers vastly simplify keeping strong and secure passwords without the need to memorising all of them.
Change your passwords periodically, especially for your most critical accounts. A known recommendation is to change the passwords once per year.
Boost your password security to safeguard your online accounts and minimize the risk of unauthorized access.
This tool will help you assess the strength of your passwords and provide insights into potential vulnerabilities. Go to website
By enabling 2FA on social media, users ensure that even if their password is compromised, the second factor (e.g., a unique code sent to their phone) acts as a digital lock, preventing unauthorized entry. This helps safeguard personal information, prevent identity theft.
2FA combines two factors to authenticate your identity: something you know (password or PIN), and something you have (smartphone, security key, authentication app). It can also include biometric factors like fingerprint or facial recognition. This multi-factor approach adds an extra layer of security to your accounts.
For Tiktok, we will use the mobile settings rather than the browser settings.
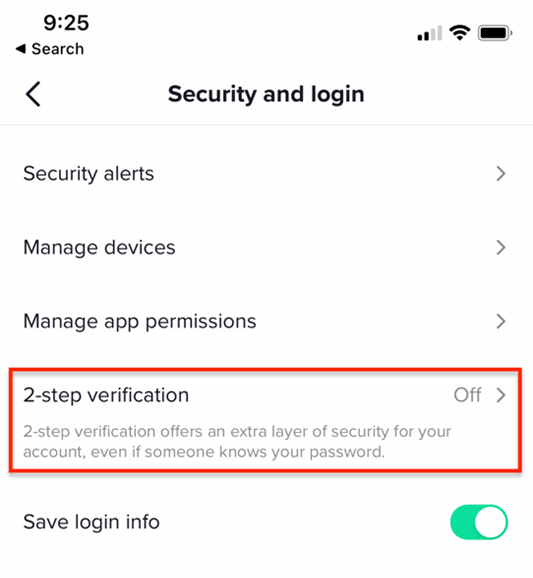
Tap the “Me” button at the bottom of the screen. Then, tap the three dots at the top of the profile screen and select “Security and login” from the menu.
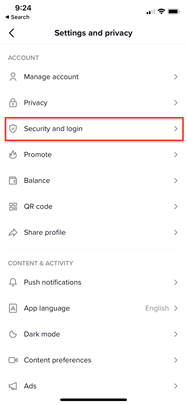
From this menu, choose “2-step verification” and click on this option.
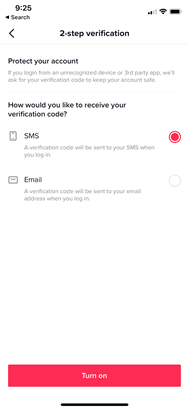
Select a method and click Turn on.
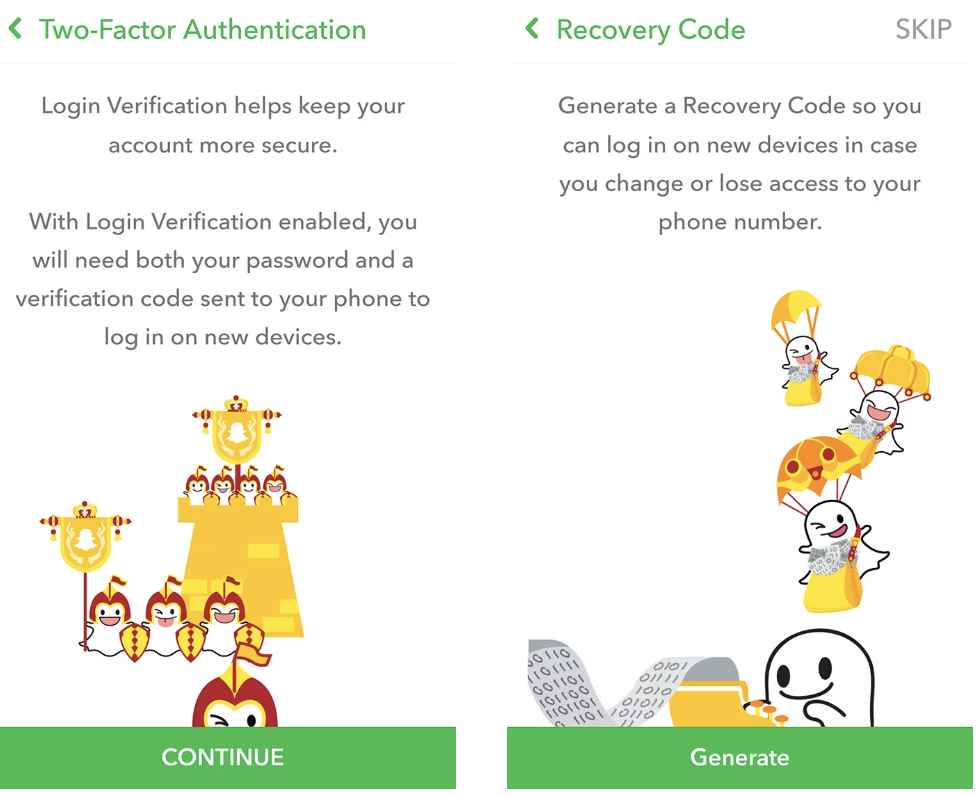
Open the Snapchat app and tap on your profile icon in the upper-left corner. Then, tap the red gear icon in the Settings menu. Look for “Two-Factor Authentication” and tap on it. After setting up two-factor authentication, remember to generate a recovery code as a backup.
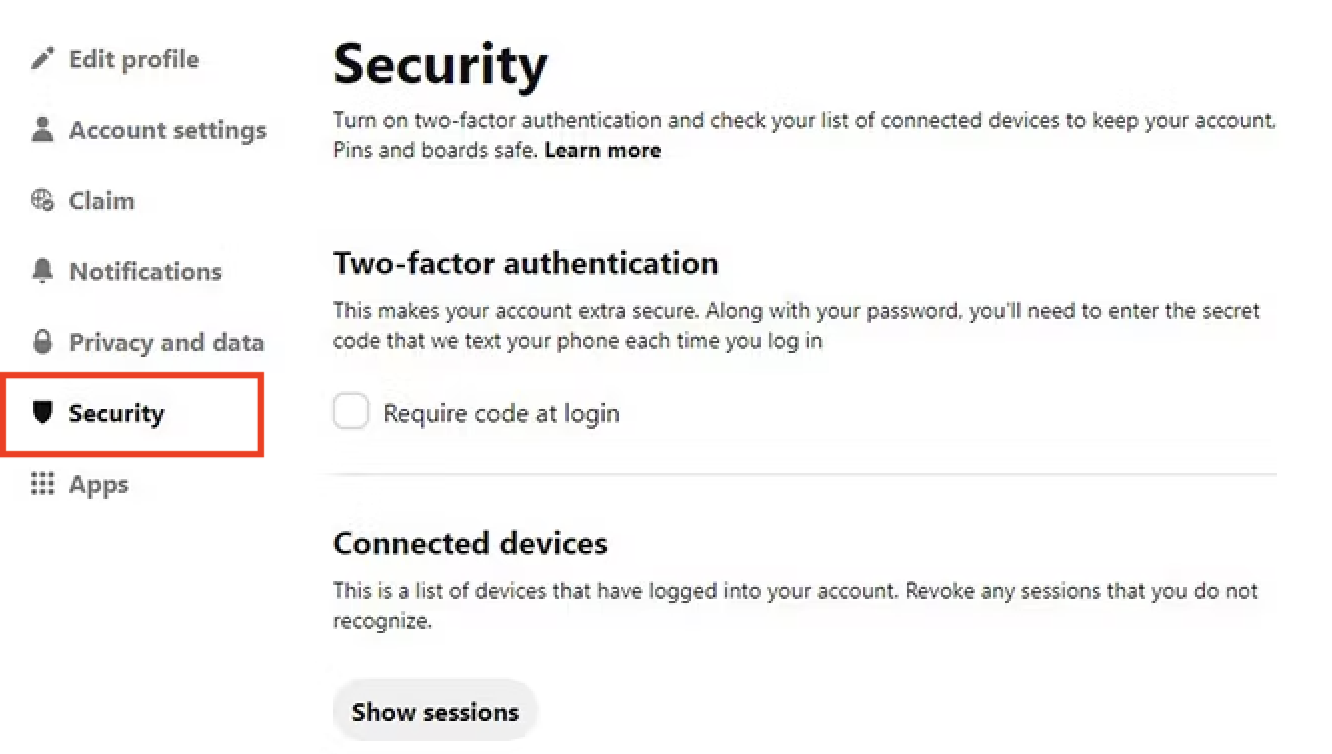
Click on your image profile on the bottom right of your screen. Then click on the 3 dots on the top right. Select “Parameters” and then “Security” in the menu. Enable the Two-factor authentification and follow the instructions.
If someone manages to obtain the user’s login credentials, they would still need the unique verification code generated by the authenticator app to gain access. This significantly reduces the chances of unauthorized access, as it requires physical possession of the trusted device or access to the authenticator app on the user’s smartphone.
Explore the world of phishing with us and learn how to stay safe from deceptive attacks. Recognize the signs and protect your personal information. Let’s outsmart the phishers and keep our online identities secure!
The art of tricking individuals into divulging sensitive information by impersonating trustworthy entities, such as banks or social media platforms, in order to gain unauthorized access to personal data or financial accounts.
1. Pay attention to the sender’s email address and look for any misspellings or unusual domain names.
2. Watch out for urgent or threatening language that aims to pressure you into taking immediate action.
3. Avoid clicking on suspicious links or downloading attachments from unknown sources.
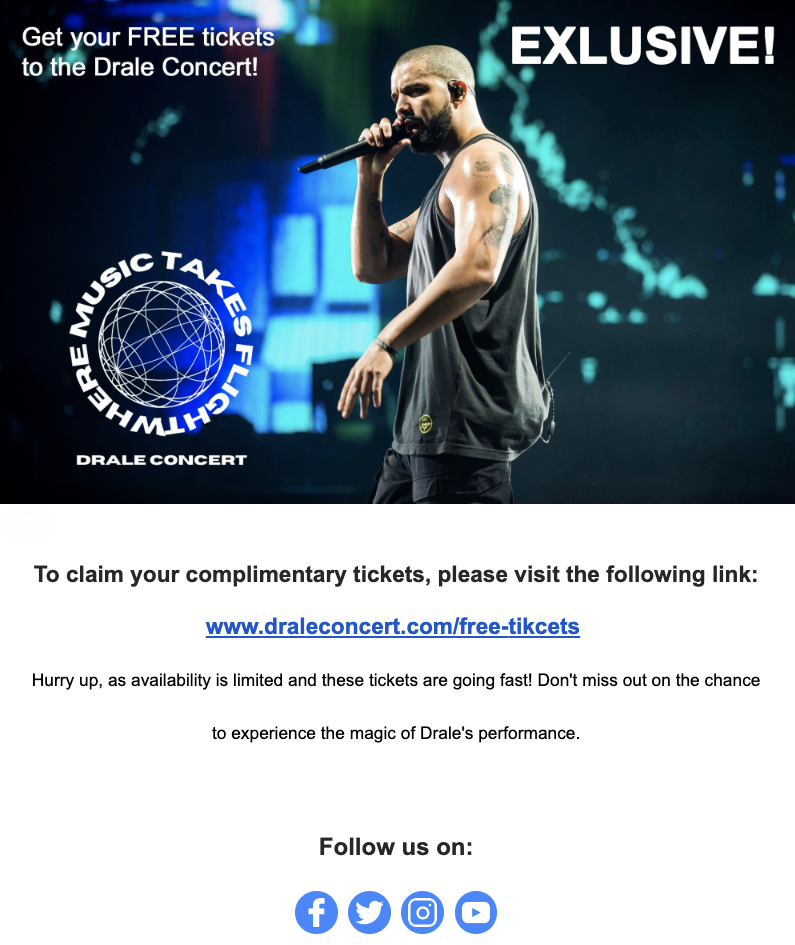

1. Double-check the website’s URL for any unusual or misspelled domain names.
2. Look for secure website indicators such as a padlock icon or “https” in the URL.
If you’re not sure you need to take an action, just connect to your account the usual way: e.g. via your app or by typing the usual URL in a browser (never with the link in the email)

Test your phishing detection skills with this interactive quiz! Take a quiz
In this step, we’ll conduct a privacy checkup to ensure your online presence is secure and your personal information is protected. Let’s enhance your privacy settings!

Adjust your social media privacy settings to control the visibility of your profile, posts, and personal information.
Disable location tracking for added privacy.
1. Control who can see your profile, posts, and personal information.
2. Limit the collection and use of your data by apps and websites.
3. Prevent unauthorized access to your accounts and personal information.
4. Stay informed about privacy policies and practices.
Adjust settings to your comfort level and protect your online privacy.
Check privacy settings in messaging apps.
Enable end-to-end encryption for secure conversations.
Disable features like read receipts or online status for more privacy.
Review web browser privacy settings (Chrome, Firefox, Safari).
Enable private browsing mode to protect browsing history.
Install privacy-enhancing browser extensions (ad blockers, tracker blockers).
Protect your privacy by regularly reviewing and updating settings.
Stay informed about new features and options for enhanced privacy.
Protect your device from malware and viruses by practicing safe downloading habits. Use trusted sources, verify file authenticity, keep software updated, and be cautious with email attachments.
Before downloading any file, make sure to verify the source and ensure it is trustworthy.
If available, check user reviews and ratings for the file or application you intend to download.
Before opening or executing a downloaded file, scan it with your antivirus software to detect any potential threats. If the antivirus software flags the file as malicious, delete it immediately.
Be cautious of suspicious sources, verify file authenticity, and keep your software updated. By taking these steps, you can maintain a secure computing environment and minimize the risk of malware and other threats.

Copyright © Université du Luxembourg 2025. All rights reserved.